Web Application Penetration Testing
Web Applications present your business, brand and services to the outside world.
They vary widely in both size and complexity from a simple business shop-front, through to providing customers with a feature rich interactive experience across web and mobile platforms.
A compromise of a web application would allow a malicious threat actor to gain access to the internal network and/or database server hosting sensitive information such as username and password information, personal data and payment card data.
Our Web Application Penetration Test provides a comprehensive means of evaluating the security of a web application. Involving a manual analysis by our CREST Certified Security Consultants identifying security weaknesses, technical flaws, or vulnerabilities, and underlying technology from the perspective of a malicious attacker in the web application and any underlying technology.
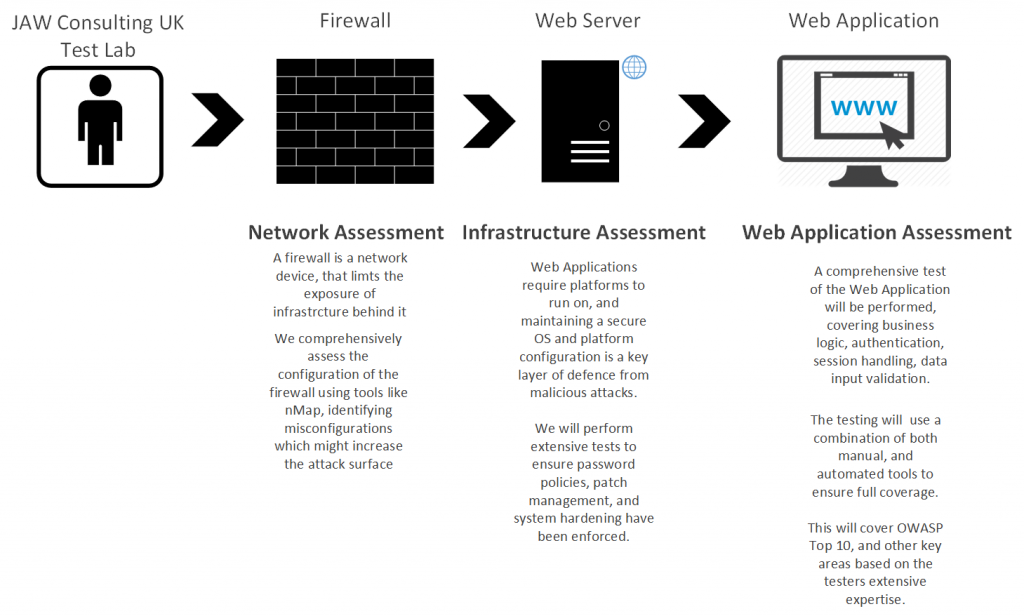
Technology in-scope of testing may include web applications, thick or client-server applications, thin (e.g. Hyper-V, Citrix) application environments, Application APIs (SOAP, REST, Social Media APIs) and the growing market of mobile apps.
A Web Application Penetration Test also covers any business logic accessible by a user or another system such as via web services (API’s).
Security issues found will be presented in a comprehensive report, together with an assessment of the impact, a proposal for remediation and/or any applicable technical solution.
The format of the report allows the business to decide on the best course of action to address the vulnerability and therefore reduce the attack surface posed by the application.
Request a Web Application Penetration Testing Quotation
Speak to Our Experts
Overview
Our web application penetration test examines every part of the web application, attempting to understand the application’s function in order to formulate realistic attack scenarios.
Guidance can be provided in advance by the client to assist our consultants with determining the best attack scenarios to try.
As part of the web application penetration testing, our security consultants attempt vertical privilege escalation from lower privileged roles, attempting to gain access to functionality and resources reserved to higher privileged roles.
Horizontal privilege escalation will also be examined where we will attempt to access resources belonging to other users. To perform this testing the client will need to provide two accounts for each role.
Additionally, your business may request us to assess applications that only communicate with other systems. These systems use APIs (application programming interfaces) that could be tricky to replicate a test harness for.
To facilitate API testing, where relevant the WSDL for the SOAP API, sample requests or the REST dictionary can be provided by your business.
Should client certificates be in use we will request your business provides a valid client certificate to allow the API to be accessed by our security consultants for testing.
The following key areas will be are covered by the methodology:
- Information Gathering
- Configuration and Deployment Management Testing
- Identity Management Testing
- Authentication Testing
- Authorisation Testing
- Session Management Testing
- Input Validation Testing
- Error Handling
- Cryptography Handling and Implementation
- Business Logic Testing
- Client Side Testing
A comprehensive web application assessment report will be produced detailing a short non-technical executive summary that will describe the security of the application as a whole.
This summary will allow budget approvers to quickly understand the risk the application currently poses and have a handle on the impacts to budget, timescales and resources any remediation will take.
The report includes full detail of each vulnerability including risk rating, ease of attack, CWE reference, if applicable a CVE reference, the CVSS v2 score and vector, and any supporting evidence. Also included is how to fix each issue.
Should multiple options exist for remediation, the pros and cons of each will be explained. If applicable, any potential problems a fix may cause will be noted. This will allow a technical person to reproduce the test findings, and be in a position to confirm if any remediation they subsequently apply actually has worked.



