Infrastructure (Network) Penetration Testing
Infrastructure (Network) Penetration Testing is a vital means of ensuring your business is protected in a real world scenario and should form part of your business’s overall Cyber Security Strategy, ensuring network based security controls and security operations are operating effectively.
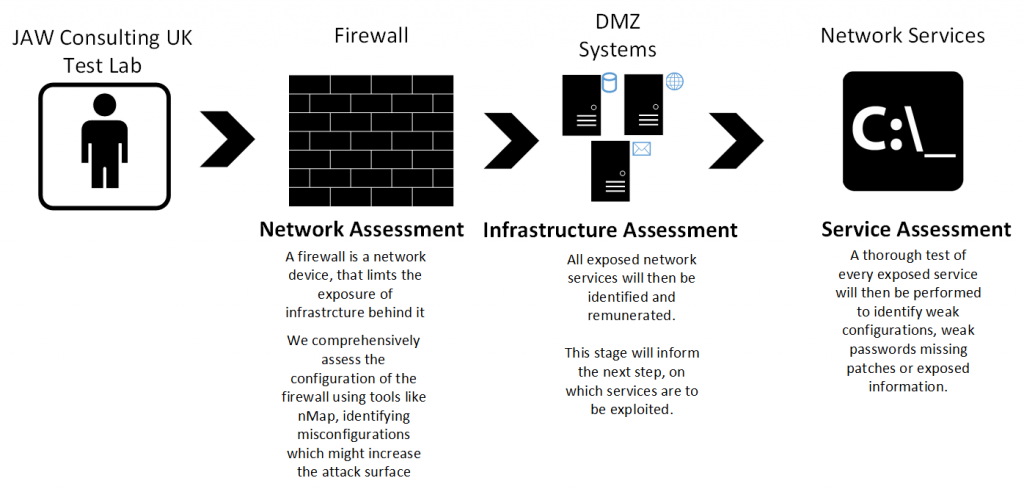
Our Infrastructure (Network) Penetration Test service replicates how a skilled and determined attacker will scour the network in search of vulnerable components (from the network to the application level).
The methodology used for infrastructure (network) penetration testing is based around ensuring your IP-based network security assessment is performed in a structured and logical way.
An assessment does not just pass once over each part of the methodology but as information is gleaned from the network, it is re-iterated over and over again until all avenues of attack have been explored in the time available.
Depending on what level of assurance is required, JAW Consulting UK can report back major issues, as they are found or seek to exploit them to demonstrate the extent a vulnerability will open up your network allowing an attacked to gain a persistent foothold.
The risks of performing an exploit to your business will be explained prior to the exploitation to allow you to make a judgement call on whether the risk is justified.
For some compliance reasons, exploitation can be a requirement and we will be pleased to discuss if this is relevant to you.
Request an Infrastructure (Network) Penetration Testing Quotation
Speak to Our Experts
Overview
There are three main types of network penetration test:
- External Infrastructure (Network) Penetration Testing: taking the view of an attacker on the Internet targeting your business’s Internet presence.
- Internal Infrastructure (Network) Penetration Testing: taking the viewpoint of an attacker who has gained access to your internal corporate network or a malicious low privilege staff member already on your network. This could include a wireless assessment if wireless is used within the business.
- Scenario Based (see below)
The table below details the areas covered in each type of assessment:
|
External Infrastructure (Network) Penetration Testing |
Internal Infrastructure (Network) Penetration Testing |
|
|
Scenario Based Testing
The above describes a breadth-first approach to infrastructure (network) penetration testing – find all the vulnerabilities.
There is an alternate different type of internal infrastructure (network) penetration test can be performed instead that isolates a single point of entry and attempts to gain as much as possible from that entry point.
This is called a scenario based test. In this test, our consultants will engage with your team to discuss their security concerns – for example, 3rd party cleaners may have access to the company office at night and your business wants to know what unattended non-staff personnel could do if they connected to the corporate network.
This is considered a bespoke engagement where our security consultants will agree a starting point for the engagement (for example begin outside the office and utilising WIFI to gain access to the corporate network) and the client will then provides a list of goals (flags) – for example to reveal the contents of a test file called ‘test’ on a restricted share or the contents of a test email sent between the CEO and CFO regarding a planned acquisition.
This type of assessment is usually time limited though the results tend to raise the case for stronger security measures within the business.
The infrastructure (network) penetration test report will detail a short non-technical executive summary that will describe the security of the network as a whole. This summary will allow budget approvers to quickly understand the risk the network currently poses and have a handle on the impacts to budget, timescales and resources any remediation will take.
The report will also include full detail of each of the vulnerabilities found including a risk rating, an ease of attack rating, if applicable a CVE reference, the CVSS v2 score and vector, and any supporting evidence.
Should a number of options exist for remediation, and the pros and cons of each will be explained. If applicable, any potential problems a fix may cause will be noted.
This format of results in the report will allow the business to decide on the best course of action to address the vulnerability and therefore reduce the attack surface of the business’s network.



